A Good Night Sleep
Knowing your business is in good hands 24×7
It's worry-free IT. With a small staff of 7, we don't have an in-house IT department and Tektonic fills that role perfectly.”
Tektonic are great in IT support. We use them extensively in our company. Would highly recommend them.”
Tektonic's customer service has always been exceptional as has their professionalism. I will always recommend them.”
Excellent customer service! They provide you with a technician as urgently as you need it without a problem.”
Excellent service. They were quick, informative and professional! Thank you!”
The team at Tektonic is excellent. Regardless of the size of your problem they're response time outstanding and customer service first rate all around!”
Tektonic has been providing professional IT Support for businesses in and around Vaughan, ON since 1998. We strive to give our clients Enterprise-level services and solutions at prices that work for businesses. Time and experience has helped us develop best practices and workflow procedures around a proactive philosophy designed to keep your focus on your business, not your technology.
Our team of experts can become your outsourced IT department; responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure, to your computers, workstations and mobile devices, we provide end-to-end solutions for all of your technology needs.
Contact us at (416) 256-9928 for exceptional IT services that will help move your business forward.


As an IT services provider in Toronto, we’re equipped to handle issues that can lead to devastating downtime or loss of function. Our tech support team has the knowledge and the advanced technology to handle the problem and get you back up and running with minimal downtime or effect on your business.
You have limited resources already as a business owner, so why use up even more of those resources maintaining something that you’re not an expert in? Why not let someone else take over the management of your Toronto IT services, freeing up your resources for other aspects of your business. You can finally free up accounting staff to do their job and let an IT professional fix the laptops, phones, and PCs.P : (416) 256-9928 • F : (647) 494-4181 sales@tek-help.com
Tektonic‚ 390 Edgeley Blvd.
Unit 19,
Vaughan, ON L4K 3Z6
A Good Night Sleep
Knowing your business is in good hands 24×7
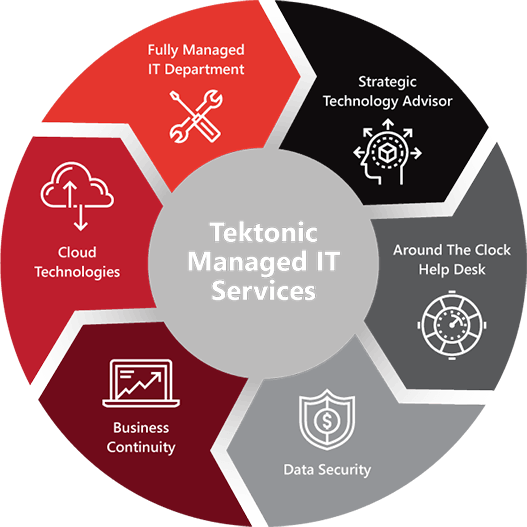
Business Continuity
Through backup and disaster recovery methods and best practices
Infrastucture Protection
Keep your network and devices safe and secure
Flat Rate IT Budget
Know your IT expenses ahead of time, your accounting department will thank you!
More Opportunities
And more time in the day to take advantage of them
Fewer Day To Day Issues
Proactive maintenance prevents issues in general
Less Downtime
Faster resolution leads to more productivity




“Tektonic has provided timely, reliable, effective and always courteous computer, network and back up support to our law firm since 2006. Our goals of protecting sensitive client information, uninterrupted productivity and ease of use of our system has been possible due to Tektonic’s proactive monitoring and management of our system.”
Lorraine Bortolussi B.A.,
LL.B., LL.M. (ADR), AccFM (OAFM)




“Tektonic has been our technology support company for several years. They are quick to respond and extremely efficient. They consider the challenges of a not for profit business in their recommendations and have worked with us to provide us with what we need to run our business efficiently. Their customer service is superb. I highly recommend this organization.”
Colleen Gouldson C.E.O.




“It is no exaggeration to say that our clinic could not function without Tektonic Inc. Almost since its inception, Tektonic has been there for us solving problems quickly and efficiently whenever we called. Not only is their response to a request for help prompt; it is always carried out in the most courteous and friendly manner. We have no hesitation in recommending Tektonic Inc. to any businesses requiring back up support for their computer (and/or telephone) systems. ”
Manager